Digital asset custody for institutions: Options and tips
The crypto market is vigorously growing, and institutional participation is on the rise. With almost 1.5B unique Bitcoin and Ethereum wallets and the recent approval of spot Bitcoin ETFs, digital assets are about to enter the mainstream. The peculiarities they bring make safe storage crucial.
The SEC's greenlighting of exchange-traded funds underscores this market's potential, maturing, and legality in the eyes of regulators. Yet, there are unique challenges in managing blockchain-based tokens, with threats ranging from loss of private keys to hacks to legal tussles.
All institutional participants, from VCs to exchanges to token issuers, seek trustworthy custodians. Cybersecurity concerns, operational complexities, and the uneven legal and insurance landscapes make regulated providers preferable. They store and safeguard digital assets, supporting transactions with advanced cryptography and hardware.
Risks of institutional custody
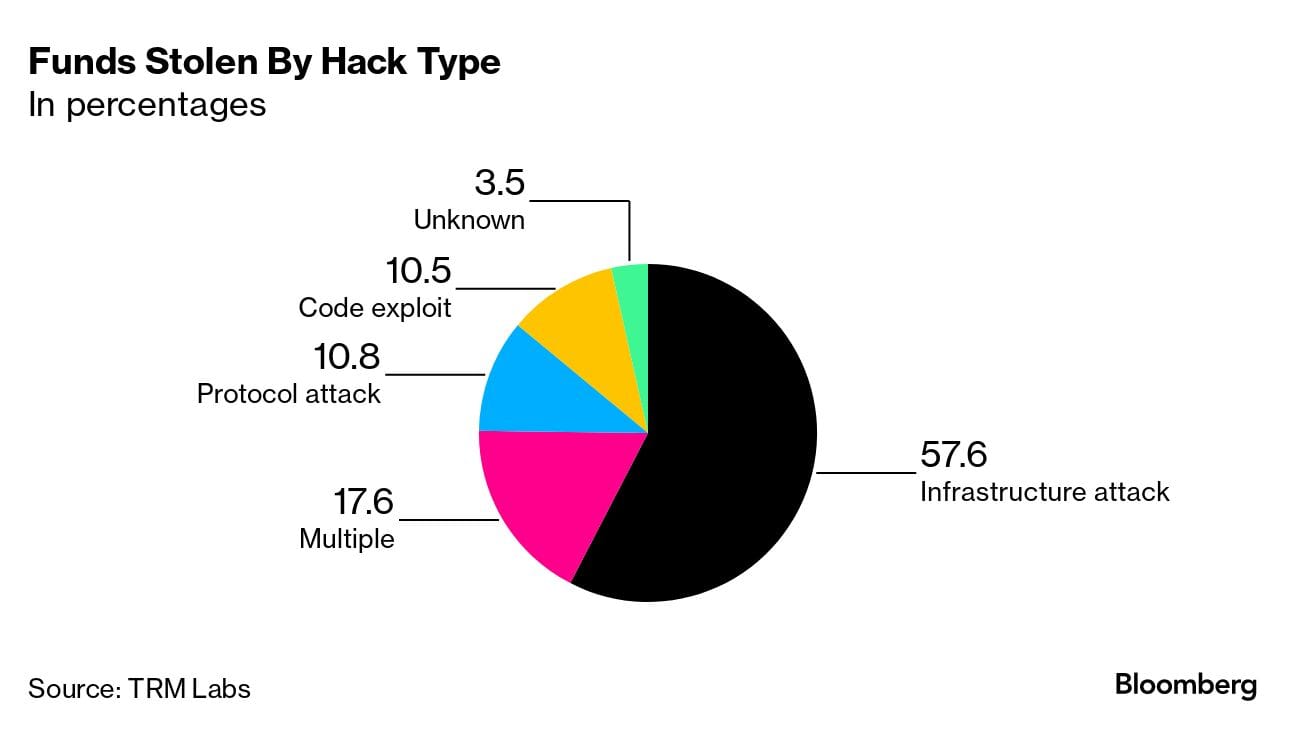
No crypto exchange is impenetrable: many leaders, including Binance, have suffered numerous attacks. While 2023 brought a significant drop in the year-on-year value of stolen funds — $1.7B against $4B in 2022 — the challenges remain. Many high-profile cases, such as the hack of the Poloniex exchange, involve private key exploits.
With self-custody, wallet owners have complete control over their private keys, but also face substantial risks. Human error and mismanagement, forgotten passwords, and hacks may result in permanent loss of funds.
The case for regulated custodians
The immutable nature of distributed ledgers makes any mistakes irreversible. Offline storage, multi-signature wallets, and other measures help custodians prevent those threats, along with issues stemming from incomplete regulations and insurance.
The following risks define the preference for regulated providers.
- Unauthorized access following loss or theft of private keys
- Irreversible mistakes related to the mismanagement of funds and data
- Irreversible mistakes stemming from the operational complexities of self-custody solutions
- Misplacement, damage, or theft of physical wallets — hardware or paper
- Hacks of crypto exchanges and insider threat
- Irreversible losses due to insufficient insurance coverage and legal protection
Classification of institutional crypto custodians
CCData’s report Crypto Custody: An Institutional Primer breaks the existing institutional storage solutions service providers into three categories depending on the services offered.
Custody technology providers
These companies supply the infrastructure (security, fund transfer and settlement, and wallets) as a foundation for in-house custody. They are neither responsible for storage nor able to access customer funds. Popular options include Fireblocks, Ledger, Taurus, and Qreda.
Hybrid custodians
As the term suggests, hybrid firms offer both custody and technology for safe storage. Customers may opt for fully self-managed custody or let them access their private keys and manage their funds if needed. Prominent hybrid custodians include Copper, BitGo, Tangany, and Hex Trust.
Regulated custodians
These providers store clients' digital assets, safeguarding their keys, data, and funds from diverse threats. They must comply with applicable laws, regulations, and best practices in their jurisdictions, such as the standards set by the US Securities and Exchange Commission (SEC).
Zodia Custody, Coinbase, Anchorage Digital, and Fidelity Digital Assets are among the market leaders.
Top 4 requirements for institutional custody
As defined by Sepior, digital asset custodians have four critical criteria to meet for a high-quality institutional-grade service. These are:
- Preventing the exposure of private keys
- Avoiding a single point of failure
- Supporting high trading volumes and high asset value
- Ensuring the agility and efficiency of crypto operations
For all four elements to work, it is crucial to minimize the trade-off between liquidity and security. Measures like multi-party computation (MPC), described below, have risen to address it.
Types of Wallets
Crypto wallets are divided into three groups based on their connection to the internet. All of them have pros and cons.
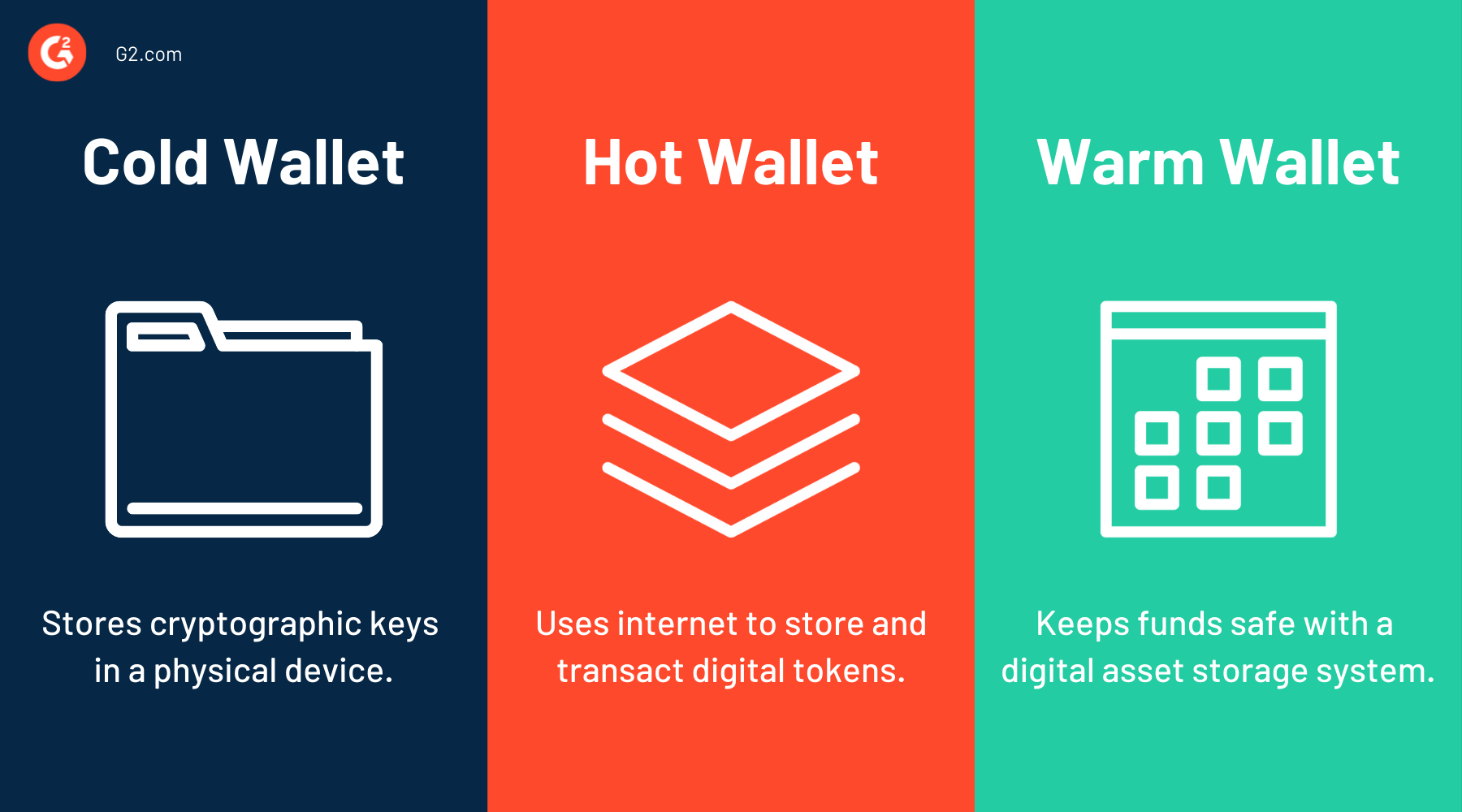
Cold wallets
Cold wallets are generally considered the safest as they remain offline most of the time. The disconnection minimizes the risk of cyber-attacks and exposing private keys to the internet. The downside, however, is a lack of scalability due to the use of dedicated hardware.
As a result, cold storage is the most attractive to pension funds, VC investors, and other entities that trade relatively infrequently based on long-term visions. Opting for security over speed, they can keep their assets unmoved until portfolio rebalancing or the conclusion of vesting cliffs. Many crypto exchanges also store most of their clients' assets offline.
Hot wallets
Wallets maintaining a connection to the internet entail heightened risks of unauthorized access through theft, mismanagement, or loss of private keys. Hacking, phishing, and social engineering attacks often target hot wallet owners.
The most significant advantage — speed — is a selling point for high-frequency traders, as they can transact immediately. This category includes hedge funds, algorithmic traders, family offices, and market makers. While they must keep a share of funds in hot wallets, over-exposure may harm their risk-reward dynamics.
Warm wallets
Some wallets aim to provide the best of both worlds through online key storage and manual intervention for approval. Before a transaction is broadcast to the blockchain, it must be signed by an authorized party. Thus, users enjoy more convenience and faster access to funds compared to cold storage.
At the same time, warm wallets rely on software kept on devices connected to the internet. Thus, despite not being online all the time, they are still susceptible to cyber attacks.
Security trifecta
Custodians implement various additional measures to boost the security of storage and asset management.
Multi-signature (Multi-sig)
Transaction authorization requires not one but multiple private keys based on a minimum threshold. Thus, by eliminating a single point of failure, multi-sig brings a tamper-evident advantage but affects scalability and operational efficiency. Some assets may not support it, yet the enhanced security makes it worthwhile for entities with complex security needs.
While multi-sig wallets may require any number of signatures, most users opt for two or three due to the technical complexities of use. This still prevents a single person, a hacker or insider, from accessing the funds.
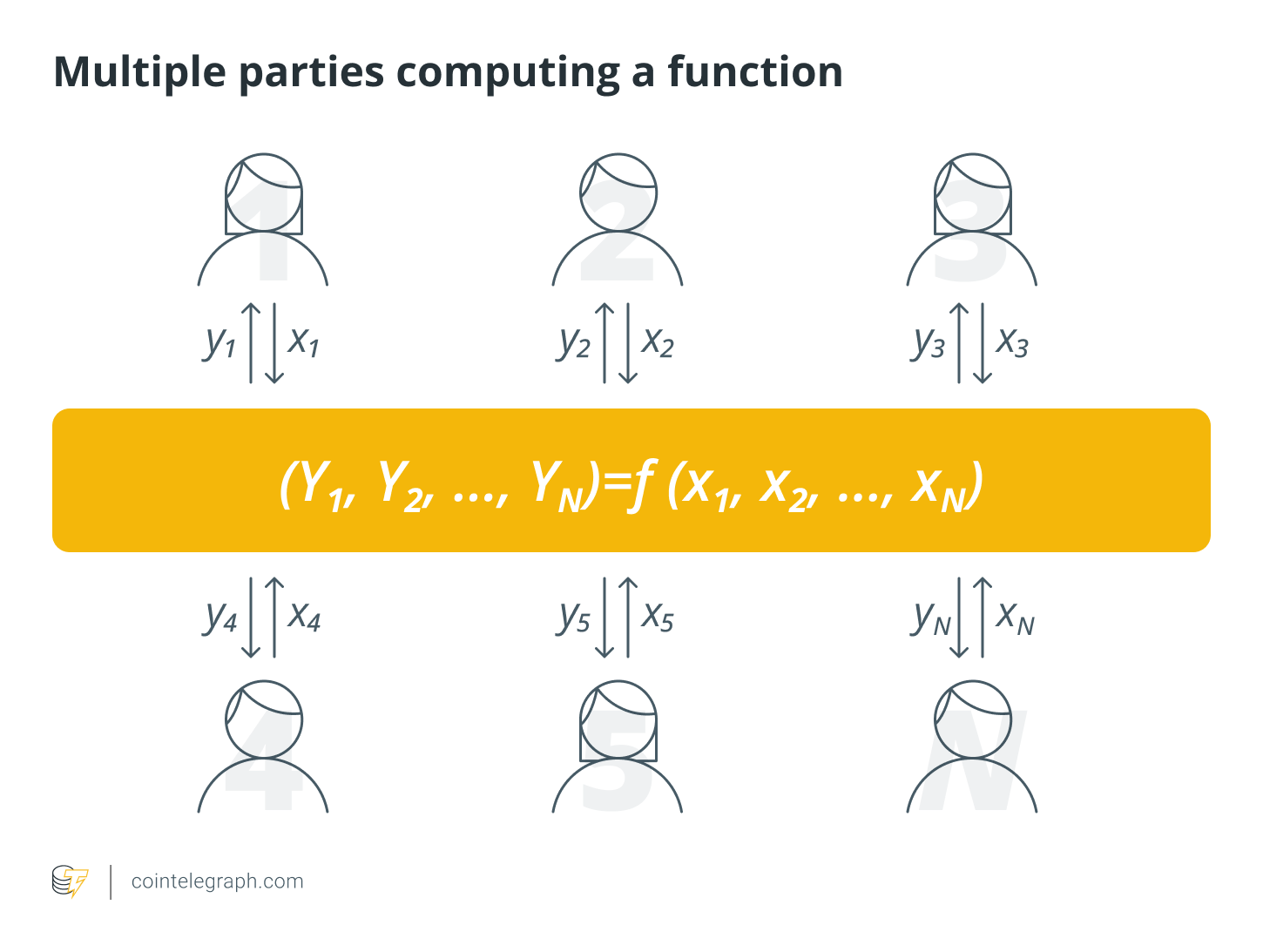
(Secure) multi-party computation (SMPC or MPC)
Instead of requiring multiple private keys, MPC systems require a certain number of key shares. They split a randomly generated key into shards – multiple parts distributed among independent nodes in a modular network. This technology is known as additive secret sharing.
MPC wallets encrypt data in transit and at rest, ensuring uninterrupted protection. The absence of physical devices also makes the systems more scalable. That said, using just one key reduces accountability, while the key generation and distribution increase the computational overhead and communication costs.
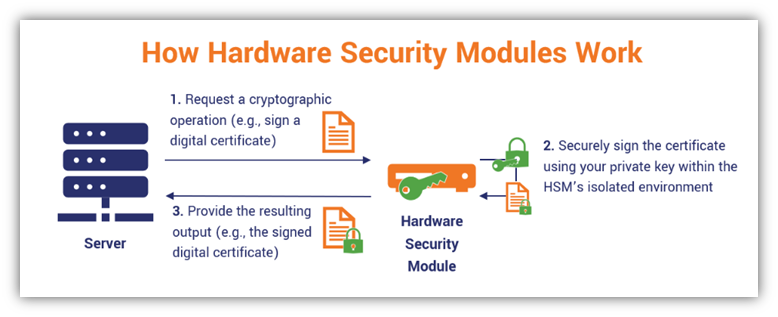
Hardware security modules (HSM)
These physical devices automate key lifecycle management based on a technology borrowed from TradFi. Keys created by random number generators are stored in an upgraded cold storage via an HSM, with access only for authorized personnel. Accessing an HSM leaves a clear trail, making it tamper-evident.
Using restricted, firewall-protected network access, HSM devices perform all crucial cryptographic operations, from encryption to key exchange. They often serve as the Root of Trust in security architecture – a source reliable at all times. As with all cold-storage solutions, the downside is the difficulty of scaling. Custodians, not the end users, deal with it.
How to choose a custodian
Apart from the storage type, institutions must consider compliance aspects and accreditations, insurance coverage, and additional benefits like staking.
Jurisdiction and licencing
Crypto regulations and legal safeguards vary around the world, as there is no universal approach to treating and classifying digital assets. The location of a regulated custodian determines the guarantees expected.
In a 2022 Fidelity survey, a third of respondents viewed regulatory classification concerns as a primary barrier to investment. A multi-jurisdictional custodian is a logical choice for companies focused on expansion with strict regulatory requirements. These providers ensure additional safeguards and certainty.
Independent audits
Third-party audits of regulated or qualified custodians are all-encompassing validations of governance controls. Independent auditors must ensure sufficient safeguards against cybercrime and unauthorized access, with proper AML and KYC measures, duty segregation, and compliance.
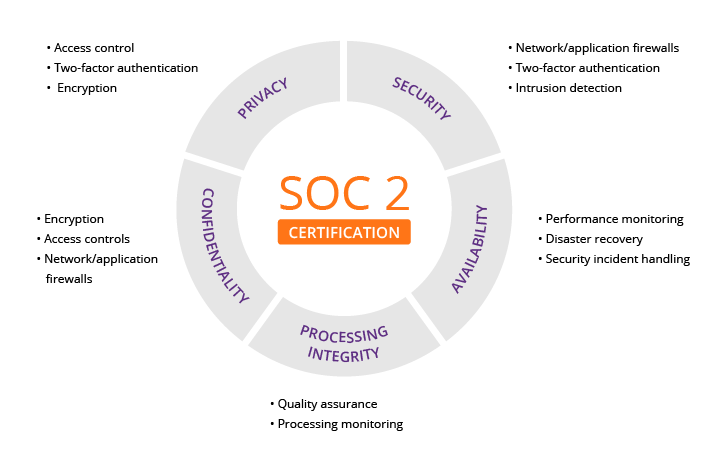
As a result of these audits, custodians may acquire industry-standard accreditations like SOC2 and ISO27001. The former focuses on security, availability, integrity, confidentiality, and privacy. It is broader than SOC1, which deals with purely financial controls.
ISO27001, backed by the International Standards Organization (ISO) and applicable to many industries, reflects compliance with globally recognized security standards and protocols.
Insurance coverage
Insurance is mandatory to mitigate third-party risk, whatever security measures are implemented. The coverage varies, but qualified custodians typically offer broader protection.
It encompasses crime insurance and cold storage insurance, along with optional safeguards: insurance against the misuse of private keys by the custodian, theft, collusion, transfer, and mistakes (errors and omissions).
Analytics and reporting
Custodians help institutions with tax reporting and transaction monitoring, which are essential for compliance.
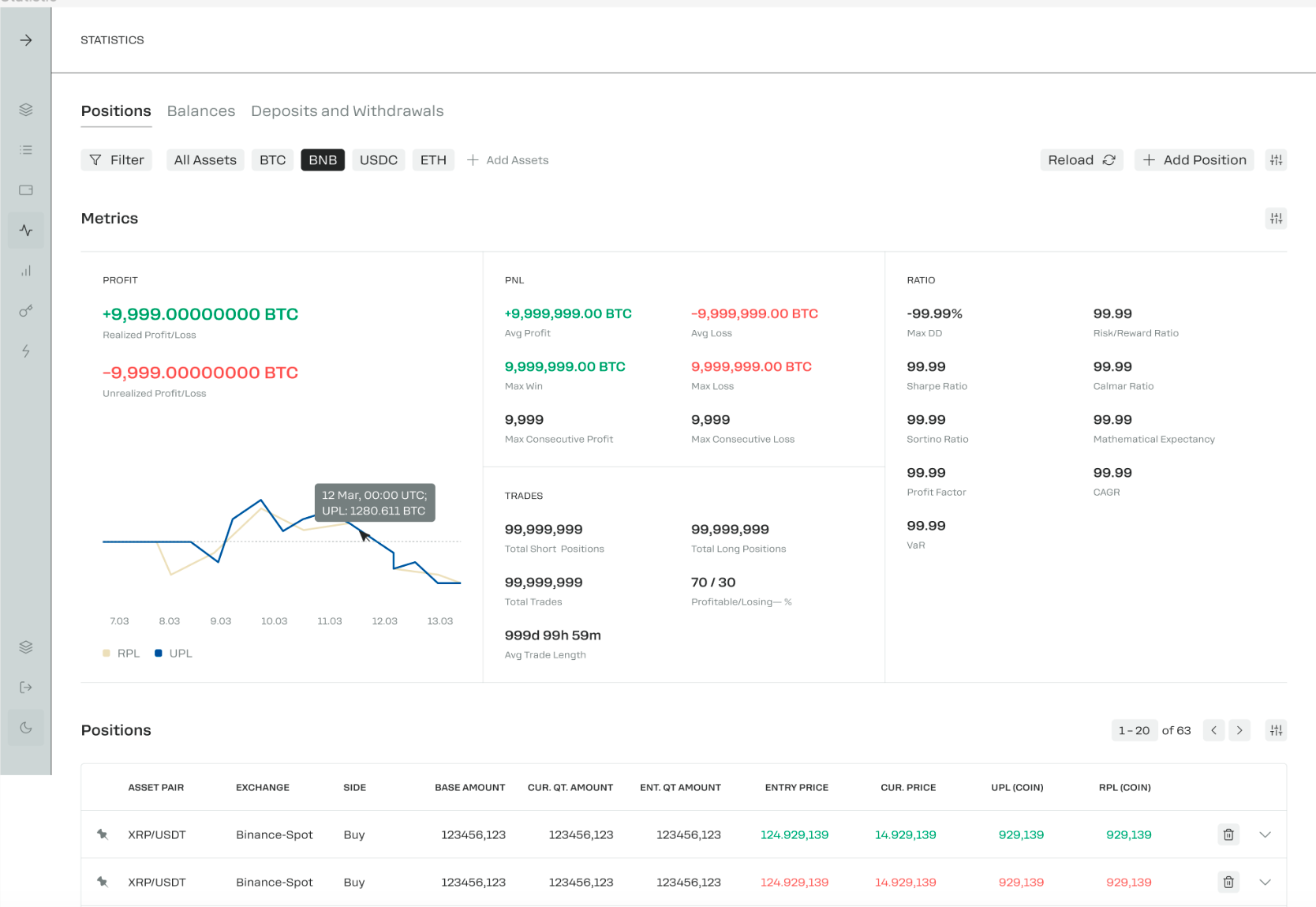
Zent also provides analytics at a granular level, well beyond profitability per trade. Volumes, PNL, and a broad array of ratios and metrics highlight insights for efficient strategies, with quick export into CSV for simplified accounting.
Off-exchange settlement
This rare and sought-after advantage is offered by custodians who partner with exchanges. The arrangement allows for funds to be held safely while being reflected natively on the platforms' front end. This innovation eliminates the trade-off between security and liquidity, but its applications have been limited.
OTC trading and prime brokerage
Some institutions opt for over-the-counter trading — without an exchange — during heightened volatility. Due to lower slippage and faster execution, it facilitates the transfer of large volumes and transactions.
However, Zent's Order Rules also address this need: execution in batches ensures orders remain invisible to market participants until a price match. Minimized market impact translates into minimized slippage.
Staking
Staking services enable institutions to earn a yield on assets locked on-chain in addition to spot profits. Due to the sheer size of institutional stakes, they substantially influence network dynamics and reward allocation.
The success of Layer-1 proof-of-stake blockchains like Ethereum, Cardano, and Solana has driven the spread of staking services since 2021. Token holders commit their assets to ensure network security in return for rewards.
By late 2023, TVL (Total Value Locked) in staking protocols had grown to over $20B. Some custodians (currently under 40%) also offer this investment feature, without the need for self-custody and the associated risks.
Custodians and the rise of tokenization
Lately, tokenizing real-world assets has been a prominent trend in crypto. Citi expects it to balloon over 80x in private markets, with a total value of $4T by 2030. Furthermore, $1T worth of the repo and securities financing and collateral market is expected to be tokenized.
In this innovative space, many assets fall under the scope of the existing TradFi regulations. Regulated custody becomes a must as they are brought on-chain. The custodians are expected to take on four key responsibilities:
- Managing tokenized assets on behalf of the issuers and investors, including issuance, distribution, redemption, and ownership record-keeping.
- Facilitating transactions by providing access to liquidity pools.
- Ensuring regulatory compliance and performing AML and KYC checks.
- Ensuring secure and transparent asset management and record-keeping.
Final words
Regulated custodians mitigate the crypto market's inherent risks through sophisticated security protocols and policies. For institutions, the implications of losing private keys or suffering security breaches are magnified, and robust custody products are crucial for broad adoption.
Given the current custody landscape, opt for qualified custody providers — regulated financial entities subject to rigorous security and operational scrutiny. The primary criteria include jurisdiction and licensing, audits and accreditations, insurance, and analytical features. Meanwhile, Zent's Order Rules and in-depth analytics eliminate the liquidity hurdles — learn more in our introductory guide.



